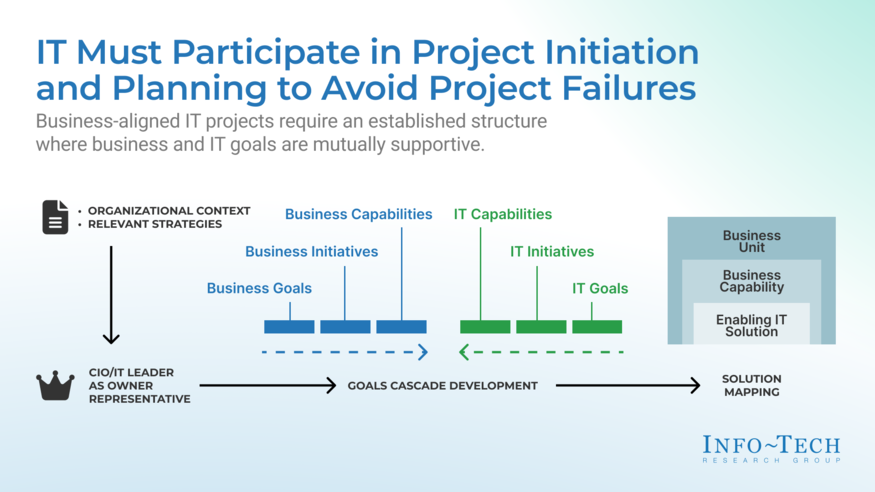
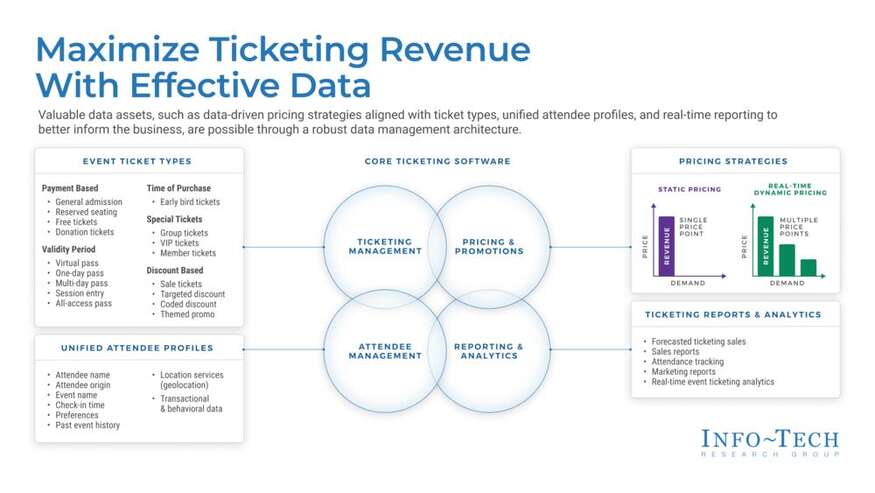
Build an Information Security Strategy
Build a Security Compliance Program
Create a Right-Sized Disaster Recovery Plan
Develop a Security Awareness and Training Program That Empowers End Users
Build Resilience Against Ransomware Attacks
Secure Your High-Risk Data
 Upcoming
Upcoming